Aurigo
Run
Even hardware problems the same as outside systems not functioning can be resolved by remote control mobile phone support as frequently the solution is to ascertain whether all gadgets are joined appropriately via the correct ports.
All claimed and done, a major facet of identifying the best sellers is a leading concern. A couple of basic points that may help determine a right vender would be:
But, the claims process can be a slippery slope. The illustrious, "Claims Department" in the assurance marketplace is witnessed as a liability, an evil sister of the firm owing to we aren't employed as revenue makers however as a matter of fact as income destroyers. Our job is to negotiate and settle the claim. We look for mitigators so, we may take the "claimed greenback amount" and reduce it, due to plan "exclusions" and anything else we will discover to reduce the amount so, it is palpable to our bosses.
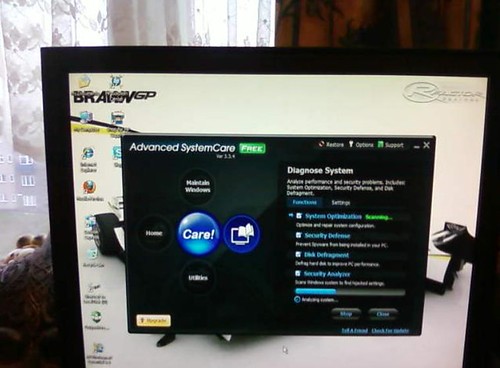
Now, let me take similar example and consider it via our Managed Expertise model. Instead of leaping in a motor vehicle to drive to the site, the technician utilizes an software to realize admission to the client's network hosting service or end-user desktop remotely and then initiates a maintenance or troubleshooting session. Let us say it's a fundamental cleanup and optimization issue. Because there is usually not a whole lot that may be carried out whereas antivirus scans are being run, or drives are being defragmented, the technician now has a chance to address more than simply this single point for this specific client.
Data encryption in the course of transmitting and computer storage ensures privateness for delicate data. There's no need for secure lockup of physical tapes. Simply as price efficiencies may be disseminated through specialised IT firms, so can certainly the most up-to-date safety procedures. Remote backup service businesses take security approaches as section of their main business, meaning their clients don't have to try to do so as well.
Binary Information Compression
Transferring solely the binary data that has developed from one day to the next, is the one other ways to additional minimize net work traffic. This is now just like the open supply file transfer service called Rsync. As an alternative to switch complete files, heightened online backup services prefer to use this method.
Lots more revealed about remote management service here.
Catherin Bettini is this weeks Remote Management Service specialist who also reveals information nile monitor lizard,usb missile launcher with webcam,avast exchange on their web site.